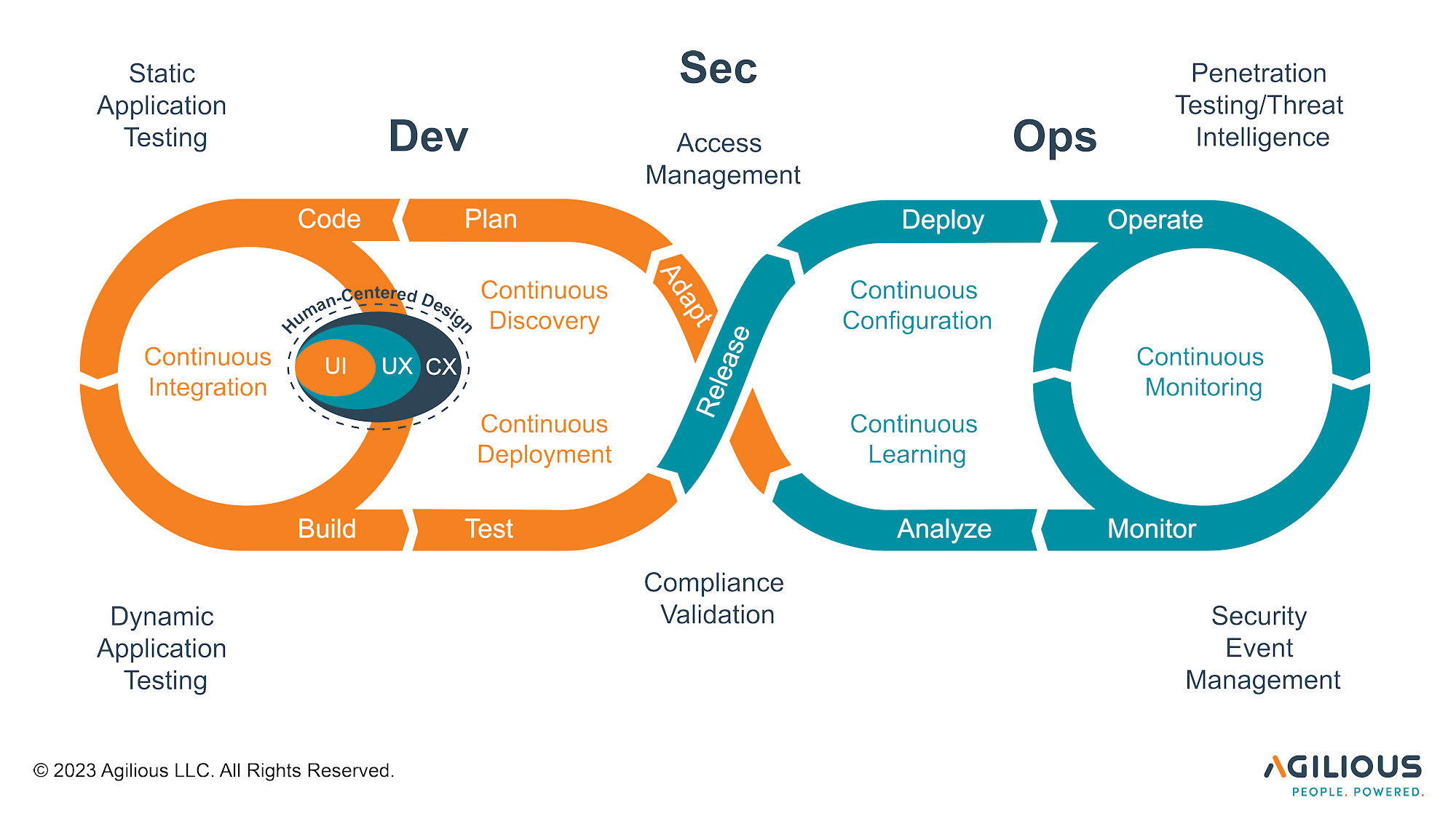
Agilious’ Lean-Agile Delivery (LeAD) Framework combines Lean-Agile Software Development, DevSecOps, and Human-Centered Design to provide benefits of iterative software development, continuous product discovery, development and delivery. The LeAD Framework integrates security practices throughout the software development lifecycle, and prioritizes the end-user experience at the core of everything we do. Our approach leads to fast delivery of secure, high-quality digital products that meet the needs of all Americans.
Elements of the LeAD Framework
![]()
Human-Centered Design (HCD)
At the core of Agilious’ LeAD Framework, is the use of Human-centered design. HCD is an approach to problem-solving that puts human needs, capabilities, and behaviors at the center of the design process. HCD in government involves designing services, policies, and systems with in-depth understanding of the needs, behaviors, and preferences of all Americans.
By applying an investigative mindset early in the HCD discovery phase, we gain insight into the end users’ thinking, emotions, and behaviors. This insight then helps in improved decision-making, thus reducing the risks by ensuring the product or service being built is solving actual problems.
![]()
Customer Experience (CX), User Experience (UX), and User Interface (UI) are integral components of HCD. These concepts work together to create solutions that not only meet functional requirements, but also align with the needs, behaviors, and expectations of the end-users.
![]()
Customer Experience (CX)
CX encompasses the entire journey of a customer (an end-user, whether a US citizen or a Federal employee), from the initial awareness of a government service to the completion of a transaction. It involves considering all touchpoints and ensuring that all users have a positive and cohesive experience with government services.
![]()
User Experience (UX)
UX focuses on delivering a positive and seamless experience for the American public interacting with government services. This includes understanding user needs, conducting user research, and designing services that are easy to use and navigate.
![]()
User Interface (UI)
UI involves the design of user interfaces that the American public interacts with when accessing government services online or offline. Clear, intuitive, and visually appealing interfaces contribute to a positive user experience.
![]()
DevSecOps
In the LeAD Framework, DevSecOps is a foundational pillar that ensures the seamless integration of security practices throughout the entire software development and delivery lifecycle. We employ a collaborative and iterative approach that involves the constant collaboration of development, security, and operations teams. From the initial stages of design and coding, security measures are embedded into the process, promoting a “shift-left” mentality that emphasizes early and continuous attention to security considerations.
By fostering a culture of shared responsibility and continuous improvement, our Lean-Agile DevSecOps framework ensures that security is not a bottleneck but an integral part of our agile and lean practices, enabling us to deliver high-quality, secure software in a timely and efficient manner.
![]()
Continuous Discovery
The LeAD Framework uses Continuous Discovery to ensure the solutions remain responsive to the ever-evolving needs of the American public. Recognizing the dynamic nature of public service requirements, our approach involves an ongoing, iterative process of research, validation, and learning.
We systematically engage in user feedback sessions, stakeholder consultations, and data analysis to gain in-depth insights into the diverse needs and expectations of the American public. By leveraging various discovery techniques, including interviews, surveys, and usability testing, we maintain a keen understanding of user experiences, preferences, and pain points. This continuous learning process allows us to validate assumptions, make data-driven decisions, and iterate on our solutions efficiently.
![]()
Continuous Integration (CI)
The use of CI significantly enhances the efficiency, reliability, and transparency of our software development process. The LeAD Framework has integrated CI seamlessly into the workflow to address the unique challenges and responsibilities associated with providing public services. This practice involves the automatic and frequent merging of code changes from multiple contributors into a shared repository. By doing so, the product development teams can swiftly identify and rectify integration issues, ensuring that the codebase remains cohesive and functional.
CI enables the delivery of high-quality software by automating the building, testing, and validation of code changes. This accelerates the development lifecycle and minimizes risk of errors, enhancing the overall robustness of the solutions.
![]()
Continuous Deployment (CD)
CD is a strategic practice that streamlines the delivery pipeline, ensuring the rapid, secure, and reliable release of software updates to meet the evolving needs of the American public. Embracing the principles of agility and efficiency, CD automates the end-to-end process of deploying code changes to production environments. This approach is particularly valuable in the context of government services, where responsiveness to evolving requirements and maintaining service reliability are paramount.
By adopting CD, the LeAD Framework facilitates a nimble and adaptive response to the dynamic nature of government services. It allows us to deliver updates with confidence, providing citizens with access to the latest and most secure features while maintaining the stability and reliability required for critical government systems. This approach represents a commitment to efficiency, transparency, and the timely delivery of innovative and secure solutions to the public.
![]()
Continuous Configuration
Continuous Configuration enhances the ability to adapt and optimize system configurations seamlessly. It involves the automated management and adjustment of system configurations throughout the software development lifecycle, ensuring consistency, security, and compliance.
Continuous Configuration also supports our commitment to transparency and auditability, enabling us to track and document changes systematically. This practice facilitates rapid adaptation to evolving requirements and mitigates the risk of configuration drift, enhancing the overall reliability of government services.
![]()
Continuous Monitoring
In the LeAD Framework, Continuous Monitoring ensures the ongoing oversight, security, and performance of the systems in adherence to rigorous regulatory requirements. It provides real-time insights into system behavior, vulnerabilities, and compliance status.
This practice involves the automated and continuous collection of data related to system operations, security events, and performance metrics. By leveraging sophisticated monitoring tools and analytics, we can detect anomalies, assess security posture, and identify potential issues promptly. Continuous Monitoring is tightly integrated into our system architecture, enabling us to respond rapidly to emerging threats or changes in the regulatory landscape.
![]()
Continuous Learning
In the LeAD Framework, Continuous Learning serves as a dynamic and proactive strategy to foster innovation, adaptability, and the sustained improvement of our processes. This practice involves an ongoing commitment to learning from every stage of the software development lifecycle. It encompasses regular retrospectives, knowledge sharing sessions, and feedback loops that encourage teams to reflect on their experiences, identify areas for improvement, and implement changes iteratively.
By actively seeking feedback from end-users, stakeholders, and team members, we gather valuable insights that inform our decision-making and guide the iterative refinement of our solutions.
![]()
Security Testing
Security testing ensures the resilience of the software systems. By integrating security testing in the development and operations pipeline, we proactively identify and address security issues throughout the DevOps process. The various testing techniques and tools we employ for security testing are described below.
Static Application Testing
The LeAD Framework integrates Static Application Testing into the development pipeline. This proactive approach leverages automated static analysis tools to scrutinize the source code for potential vulnerabilities and security flaws before the application is even executed. By embedding Static Application Testing seamlessly into our CI and CD processes, we ensure that security assessments are conducted consistently with each code change.
Dynamic Application Testing
The LeAD Framework integrates Dynamic Application Testing seamlessly into the CI and CD pipeline. This practice automates analysis and evaluation of running applications to identify potential vulnerabilities and security weaknesses in real-time. Using this testing, we can systematically assess the applications for security risks throughout the development lifecycle. The insights gained from dynamic testing empower the teams to remediate vulnerabilities promptly, fostering a proactive and collaborative approach to secure application development.
Compliance Validation
The LeAD Framework integrates Compliance Validation seamlessly into the CI and CD pipelines. This practice applies systematic validation of the software and infrastructure against established regulatory and compliance standards. This proactive approach mitigates risks associated with non-compliance and streamlines the validation process, allowing the teams to identify and address potential issues in real-time. Compliance Validation is a crucial component of our commitment to delivering secure and trustworthy solutions, aligning our development practices with the highest standards of compliance
Security Event Management
The LeAD Framework, integrates Security Event Management into the Continuous Monitoring Process. This practice involves the real-time monitoring, analysis, and response to security events across the applications and infrastructure. This approach allows the teams to identify anomalous activities, potential vulnerabilities, and security breaches promptly, enabling rapid remediation. Security Event Management is a key element of our commitment to a secure development environment, aligning with our dedication to delivering resilient software that withstands evolving cybersecurity challenges while adhering to the highest standards of security and compliance
Penetration Testing
The LeAD Framework, integrates Penetration Testing into the Continuous Monitoring Process. Penetration Testing, often known as ethical hacking, involves simulating real-world cyberattacks to assess the security resilience of the software. This proactive approach ensures that the applications can withstand sophisticated attacks and adhere to the highest standards of security. Penetration Testing is instrumental in fortifying our commitment to delivering robust, secure, and resilient software, aligning our development practices with the evolving landscape of cybersecurity threats and compliance requirements.
Access Management
The LeAD Framework, integrates Access Management into the Continuous Security Process. This practice involves the strategic control and monitoring of user access to the systems, applications, and data. This proactive approach minimizes the risk of unauthorized access, potential data breaches, and ensures compliance with security policies. Access Management is a key element of our commitment to a secure development lifecycle, aligning our practices with the best standards and regulations in the industry. This robust approach enhances our ability to deliver software that meets functional requirements and adheres to the highest standards of security and compliance.