Agilious is putting DevSecOps and Agile Software Development into practice with our Federal Health client, Food and Drug Administration (FDA). Our support today is aligned with the FDA’s Technology Modernization Action Plan (TMAP). Specifically, it supports two of the three goals outlined in the TMAP: (1) modernization of FDA’s technical infrastructure; and (2) enhancing FDA’s capabilities to develop technology products to support its regulatory mission.
Agilious has streamlined software development capabilities for business-specific needs (“DevOps”) of FDA’s mission. In the current landscape of software development, security is an integral part of the development process. As Agilious develops more and more complex modern applications, we are ensuring that security is seamlessly integrated into every stage of the software development-operations (DevOps) life cycle.
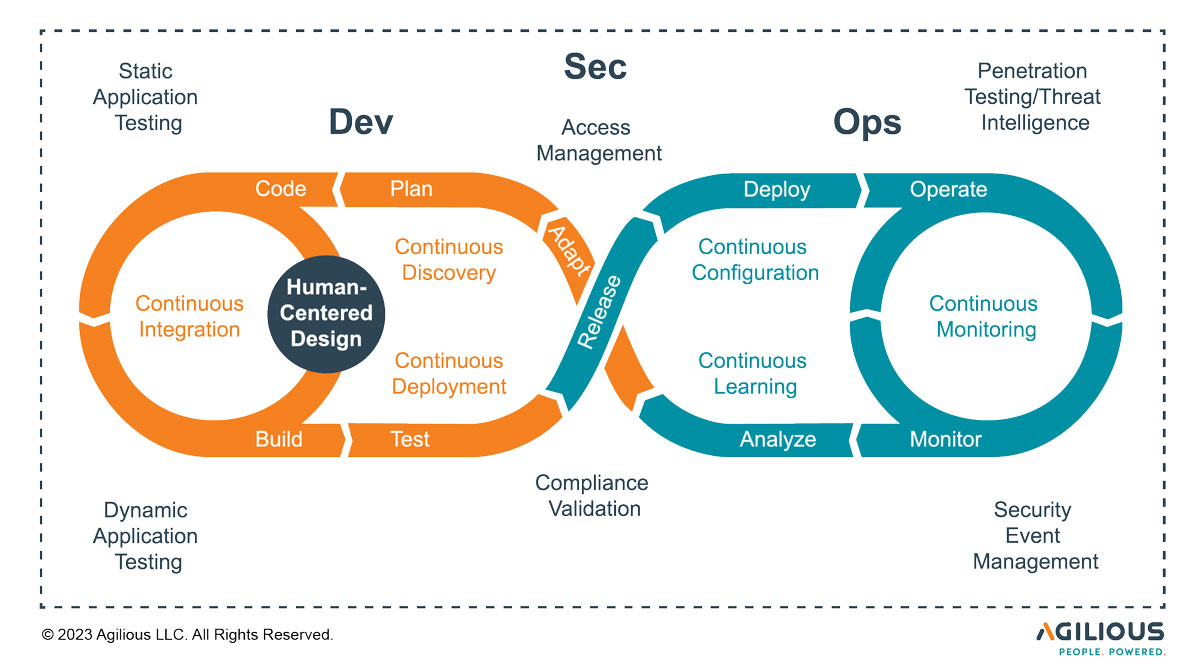 What is DevSecOps?
What is DevSecOps?
DevSecOps is a set of practices that unifies software development (Dev), security (Sec), and IT operations (Ops) to shorten the software development life cycle and ensure continuous, high-quality delivery. It emphasizes a shift-left approach, meaning that security is embedded from the very beginning, making it an integral part of the development process.
The Shift-Left Approach
In traditional software development, security was often an afterthought, leading to vulnerabilities that were costly to fix. DevSecOps flips this model by integrating security into the development process, allowing for early detection and mitigation of security issues. This approach reduces risks, shortens development cycles, and enhances overall software quality.
Key Principles of DevSecOps
DevSecOps is built on these key principles:
- Automation: Implement automation tools to ensure security checks are performed throughout the development pipeline. This includes code analysis, vulnerability scanning, and compliance checks.
- Collaboration: Foster collaboration between development, security, and operations teams, so that security issues are identified and resolved effectively.
- Continuous Monitoring: Real-time monitoring of applications and infrastructure for security threats, so that the threats can be detected and responded to early.
- Immutable Infrastructure: Use Infrastructure as Code (IaC) and containerization to make infrastructure changes predictable and consistent, reducing the attack surface.
Security Tools and Technologies
DevSecOps relies on a range of tools and technologies to implement security measures effectively:
- Static Application Security Testing (SAST): SAST tools analyze the source code for vulnerabilities, helping developers catch security issues early in the development process.
- Dynamic Application Security Testing (DAST): DAST tools test running applications for vulnerabilities, providing insights into real-time threats.
- Container Security: Implement security measures for containers, including image scanning, runtime protection, and network segmentation.
- Infrastructure as Code (IaC) Security: Secure infrastructure by using IaC practices and tools that ensure configuration compliance and protect against drift.
Benefits of DevSecOps
- Faster Time to Market: By integrating security from the outset, development teams can deliver features faster.
- Reduced Cost: Early detection of security issues and automated remediation reduce the cost of addressing vulnerabilities.
- Enhanced Reputation: Robust security practices protect an organization’s reputation by preventing data breaches and cyberattacks.
- Regulatory Compliance: DevSecOps practices help meet compliance requirements more efficiently.
- Continuous Learning and Adaptation: DevSecOps is a dynamic field, and security threats evolve constantly. Therefore, continuous learning and adaptation are essential. Stay updated with the latest security trends, tools, and best practices to ensure that your DevSecOps processes remain effective.
In conclusion, DevSecOps is a critical discipline in today’s software development landscape. It offers a proactive and holistic approach to security, helping organizations build secure, reliable, and resilient software applications. By embracing the shift-left approach, adhering to key principles, and leveraging the right tools and technologies, you can empower your team to develop, deploy, and maintain software that stands up to the ever-present threats in the digital world.
Are you using DevSecOps? Are you applying the key principles and leveraging the right tools and technologies?
Share your experiences with us at https://www.agilious.com/contact-us/.






